Infostealers are an emergent type of malware, and they’ve become all the rage recently in the cybercrime underground. Whilst you may not have heard of infostealers, infostealers have probably heard of you. Cybercriminals infect your devices with an infostealer by having it masquerade as a legitimate file available for download online or any other myriad of ways. This could be through a phishing email or a torrent file, among other ways.
They’re such a serious threat that the FBI, Dutch national police and other partners recently acted to take down two of the leading infostealer families, Redline and Meta (https://therecord.media/infostealer-servers-takedown-dutch-police-fbi). Infostealers have infected tens of millions of victim machines in both the public and private sectors, and the exfiltrated data aids cybercriminals in launching ransomware attacks, blackmail individuals, and even take over companies’ networks.
In contrast to regular data breaches in which only your account on a given platform or service is leaked , Infostealers harvests a victim’s computer content, including autofill data, saved personally identifiable information (PII), financial data, and log in information. Passwords, social media accounts, banking information, keyword searches areamong the sensitive data that could be stolen. The data is then aggregated on cybercriminal servers, packaged, and sold (or leaked ) on the online criminal ecosystem.
Infostealers Pattern of Life:
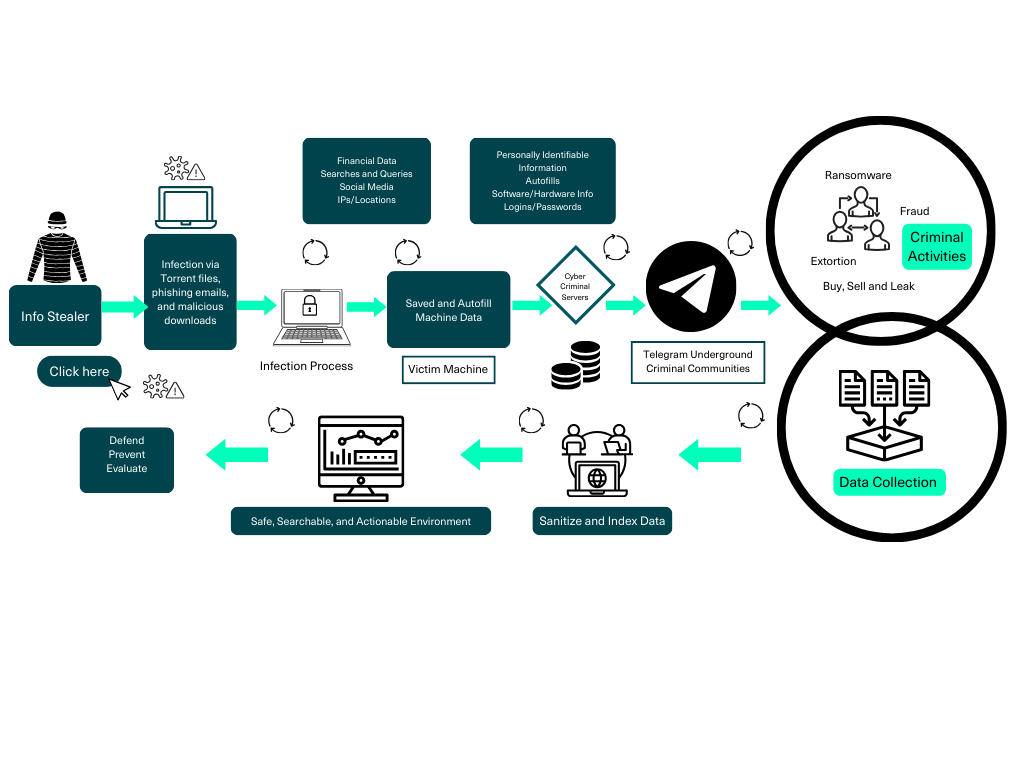
Like everything, however, there’s another side to the story. Data services that aggregate infostealer logs, such as Tesseract Intelligence, Hudson Rock and District 4, make this information available and searchable to those with a legitimate reason – primarily protecting yourself and your organization from breaches. However, researchers can also use infostealers for investigative purposes, such as identifying users that have accessed dark web sites to view child sexual abuse material (CSAM).
This investigative piece is the result of collaboration between Falkor and the MVP Taskforce, showcasing the investigative power of infostealer logs. Be it for law enforcement, trust and safety teams and anyone else involved in investigating, mitigating, and countering CSAM, human trafficking and more, infostealer logs can be a critical source of information, especially by fusing Falkor’s data visualization and AI capabilities with leading OSINT tooling and APIs.
The investigation begins with a sample stealer log identified by the MVP Task Force as having access child exploitation sites.
Ingesting the log into Falkor
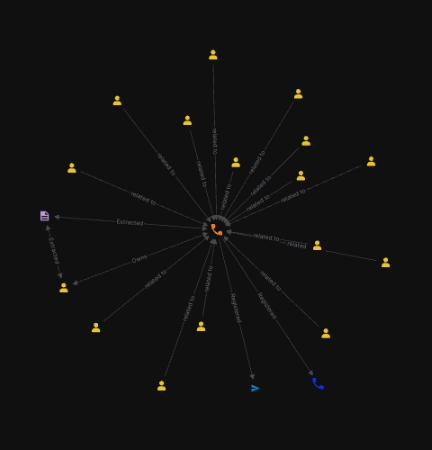
We can upload the infostealer log file into Falkor as raw JSON or other filetypes. Once ingested, the entities are extracted and related to each other. At this stage, we have the below entity types:
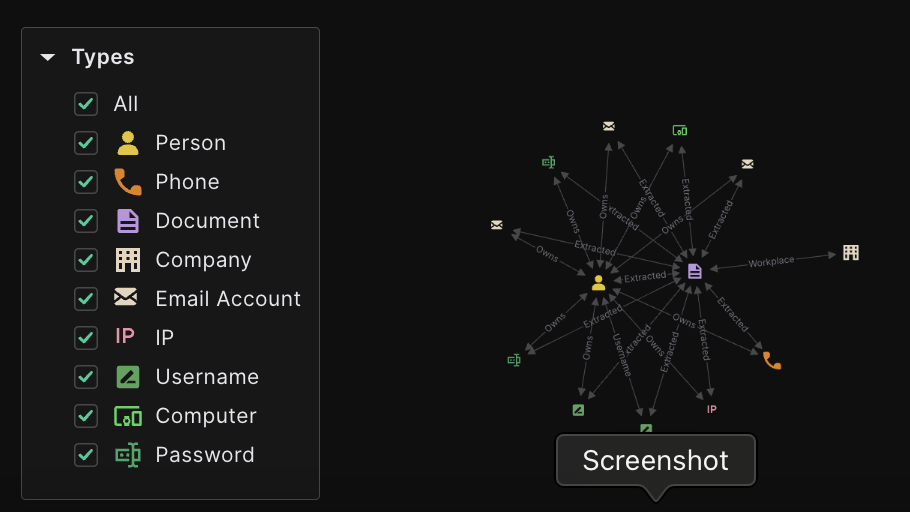
This is already a lot of data in of itself. Most importantly, the data included is of high quality and often reserved for those with proprietary data sources as well, such as the suspect’s IP address, password(s) and device information. However, at this stage we don’t have enough to identify the suspect conclusively, as they have used a burner phone, burner email addresses and false information in their past registrations.
Here, we begin the investigation via Falkor’s integrated OSINT APIs. Falkor supports dozens of OSINT API endpoints, with more constantly being added. We use Falkor’s enrichment capabilities to simultaneously enrich all the above datapoints with multiple OSINT data-sources. This is a superior process when compared to manual investigations, in which each datapoint would have to be painstakingly queried in dozens of different sources for maximal enrichment.
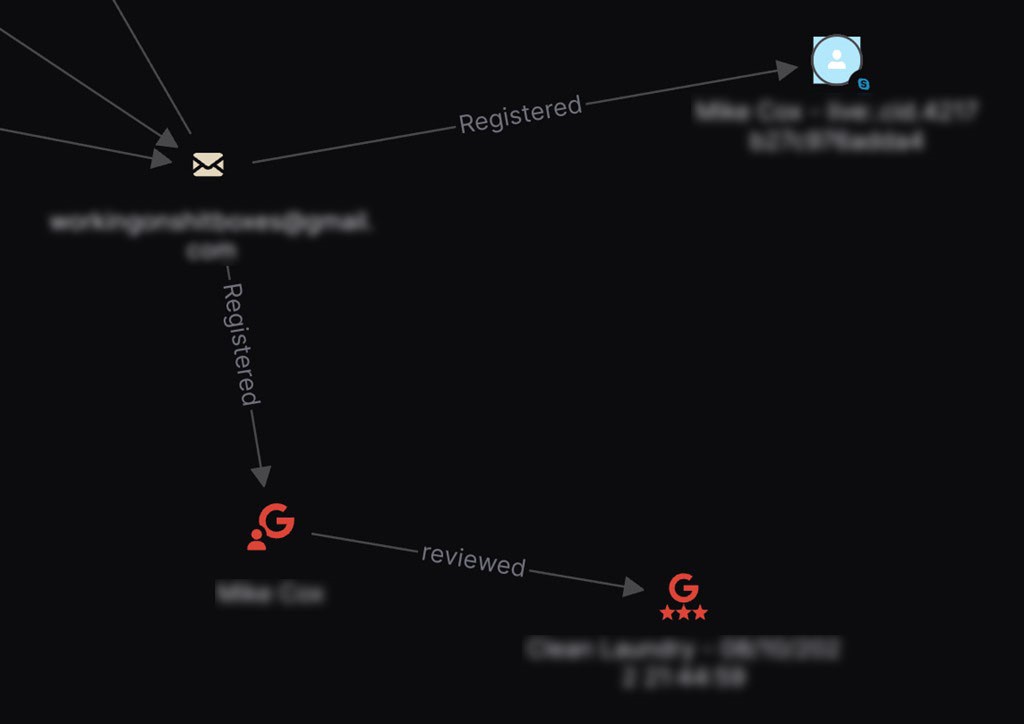
The first datapoint that we’ll enrich is the main burner email used by the suspect.
The email address is a burner, but by enriching it in OSINT Industries, we receive a Skype and Google accounts with the suspect’s name. More importantly, we see that the suspect has made the mistake of leaving a Google review several years ago under this email address, giving us a clue as to the suspect’s whereabouts.
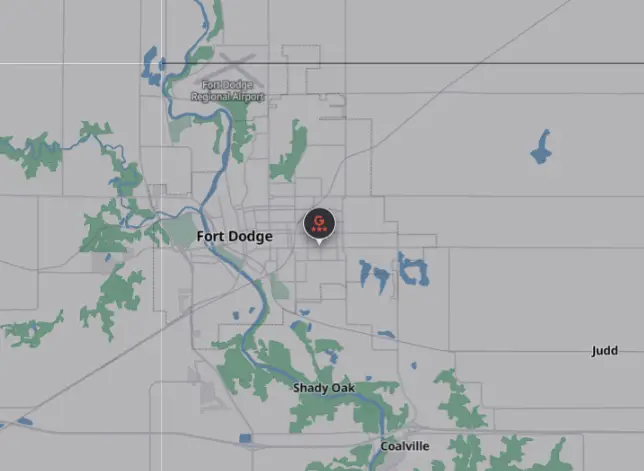
We can view the location reviewed as well on Falkor’s map:
The suspect’s phone number also has significant value for enrichment. Enriching the phone number in Falkor’s OSINT APIs, including OSINT Industries, Epieos, Pipl, District 4, returns multiple affiliated individuals and names used in conjunction with the phone number. In addition, we uncover one TrueCaller record as well as an affiliated Telegram account. This information can be easily expanded upon going forward with warrants or other OSINT searches, or by investigating the affiliated Telegram account.
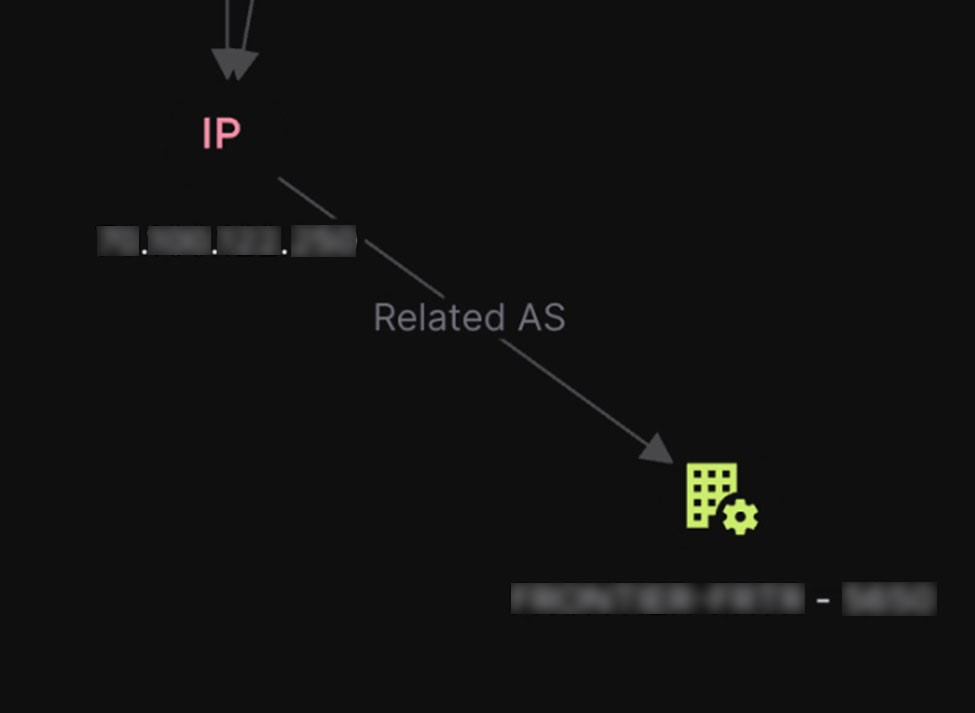
The IP address that the suspect used at one point to register an account is also something that we can enrich in Falkor. We can look up the IP address to determine its rough geographic location, as well as receive information on the ISP:
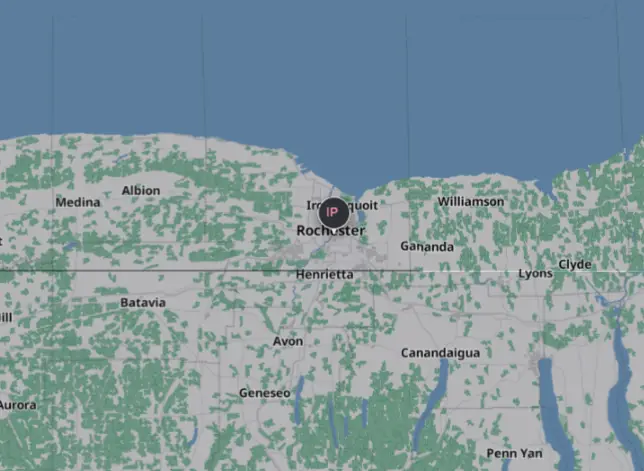
By viewing it on the map, we can see that it doesn’t match up to our previous Google review result:
We can use the remainder of our information to find out more about our suspect and finalize his general area.
We can use compromised data for example, aggregated by District 4 Labs, in Falkor to further enrich suspect data such as leaked passwords. Enriching one of the suspect’s passwords finds multiple leaked databases in which the same password was used, retrieving additional datapoints that may belong to the suspect:
The suspect also has an Instagram account, identified by pivoting on the previously available datapoints. By using Falkor’s OSINT integrations, we can gather data on followers, post and other activity on the suspect’s Instagram account.

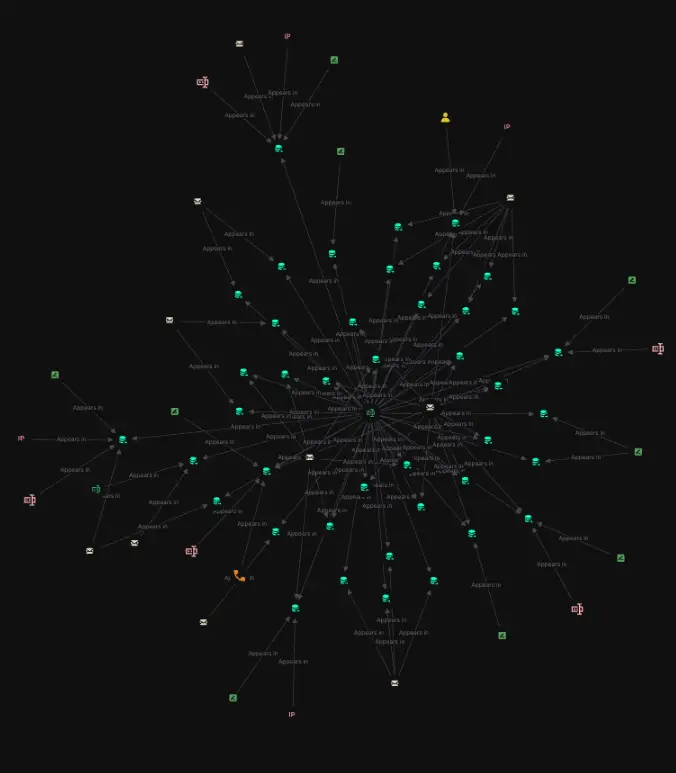
Once we have our initial findings, we can begin cleaning up the link analysis palette to remove extraneous information. Below, we have the first draft of what an initial investigation into the suspect would look like, in this case done in under 30 minutes!
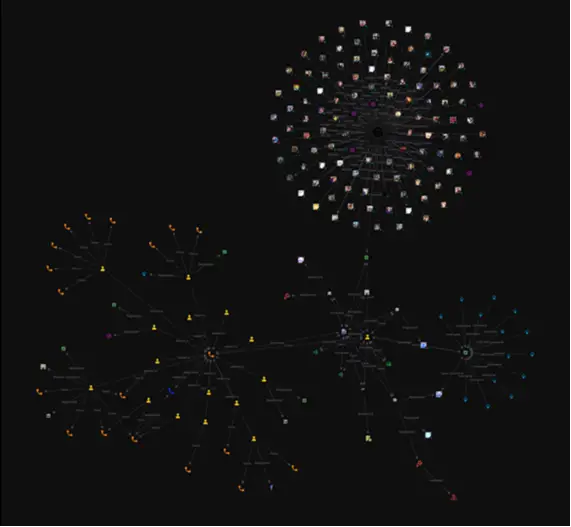
The power of infostealers is undeniable. Infostealer logs include a wealth of information and enable investigators to proactively identify offenders in a variety of categories.
During the course of this investigation, researchers have been able to unveil the identity of the suspect and enrich the available information with additional data points that law enforcement agencies can now use to issue warrants and build evidentiary support material.
Furthermore, this investigation clearly showcases the power of collaboration between NGOs and the technology sector, fusing knowledgebase, data sources, and speed to uncover criminal activities. This work sets the stage for more collaborative investigations, underscoring the constant need for signal rich data, skilled analysts, and technology optimization.
At MVP Task Force and Falkor, we are united by a shared mission to combat malicious activities, with a special focus on protecting the most vulnerable among us. By leveraging the robust capabilities of the Falkor platform, harnessing data rich in actionable signals, and relying on the unwavering dedication of committed analysts, we exemplify how collaboration drives impactful results in safeguarding our communities.



